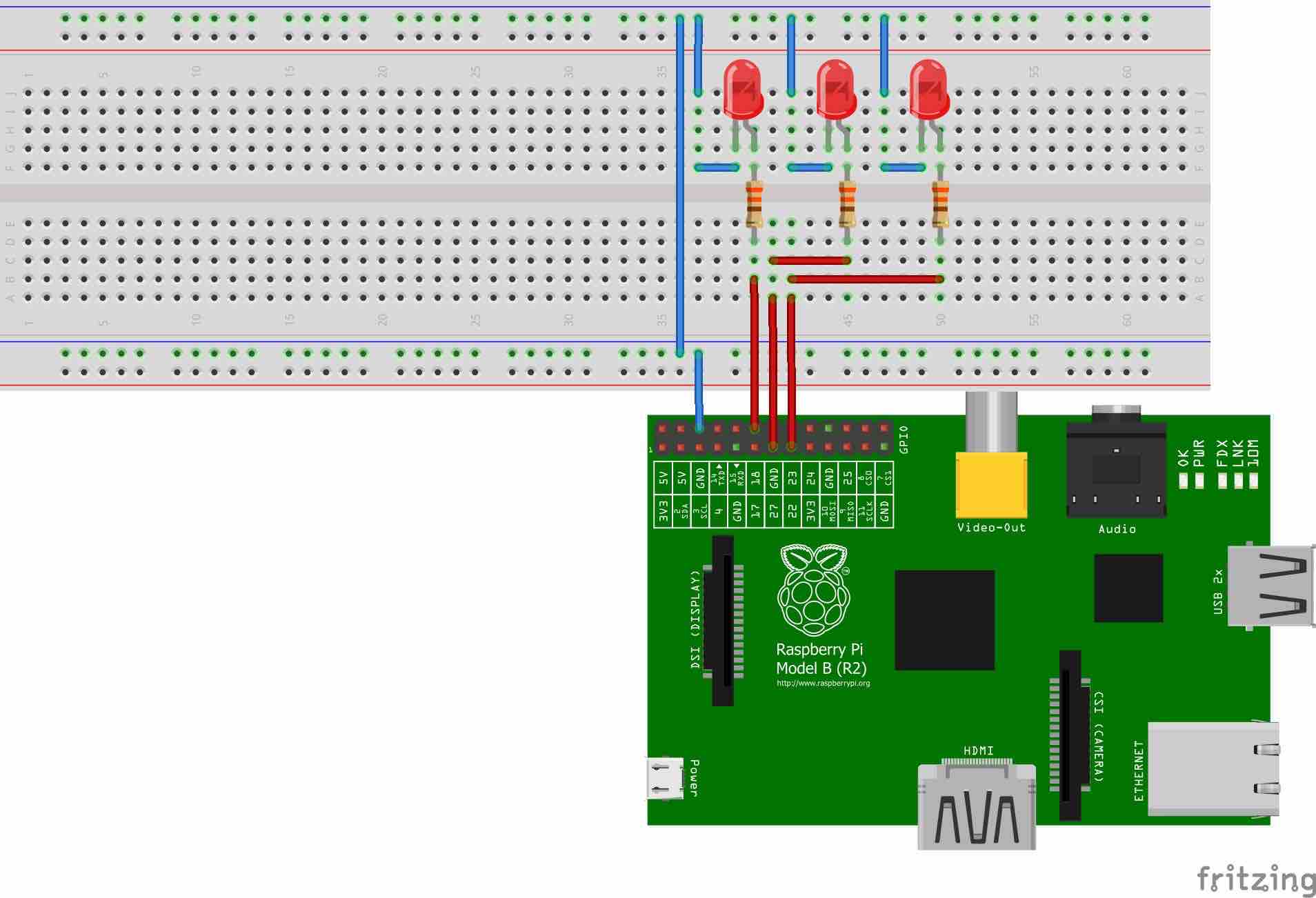
In today's interconnected world, leveraging SSH for IoT remotely free solutions is essential for businesses and individuals alike. Secure Shell (SSH) offers unparalleled security and control for managing remote devices, especially in the Internet of Things (IoT) ecosystem. With the growing demand for cost-effective solutions, understanding how to implement SSH for IoT devices without incurring high costs is crucial.
SSH has become a cornerstone for secure data transmission across networks. Whether you're a tech enthusiast, a small business owner, or a professional developer, knowing the best SSH IoT remotely free options can help streamline your operations. This article delves into the tools, techniques, and best practices for implementing SSH for IoT devices without breaking the bank.
From understanding the basics of SSH and IoT to exploring free tools and services, this guide aims to equip you with the knowledge needed to manage your IoT devices securely and efficiently. Let's dive in and discover how you can harness the power of SSH for IoT remotely free.
Read also:Building A Raspberry Pi Vpc Network A Comprehensive Guide
Table of Contents
- Introduction to SSH and IoT
- Benefits of Using SSH for IoT
- Choosing the Best SSH IoT Remotely Free Options
- Tools for SSH IoT Remotely Free
- Setting Up SSH for IoT Devices
- Securing Your SSH IoT Connections
- Common Issues and Troubleshooting
- SSH IoT Best Practices
- Future of SSH in IoT
- Conclusion and Next Steps
Introduction to SSH and IoT
Secure Shell (SSH) is a cryptographic protocol designed to provide secure communication over unsecured networks. It has become an industry standard for remote access and file transfer due to its robust encryption and authentication mechanisms. The Internet of Things (IoT) refers to the network of interconnected devices that communicate and exchange data without human intervention.
Why SSH is Essential for IoT
SSH ensures secure communication between IoT devices and central servers. With the rise in cyber threats, securing data transmission is paramount. IoT devices often operate in open environments, making them vulnerable to attacks. SSH offers encryption, authentication, and integrity checks that mitigate these risks.
Key features of SSH in IoT include:
- End-to-end encryption for secure data transmission.
- Strong authentication methods to prevent unauthorized access.
- Support for various protocols and platforms, ensuring compatibility with diverse IoT ecosystems.
Benefits of Using SSH for IoT
Implementing SSH for IoT devices brings numerous advantages, especially in terms of security, efficiency, and cost-effectiveness. Below are some of the key benefits:
Enhanced Security
SSH encrypts all data transmitted between devices, ensuring that sensitive information remains protected from unauthorized access. This is particularly important in IoT environments where devices often communicate across public networks.
Read also:Free Remote Access For Iot Devices And Raspberry Pi Through Ssh
Efficient Remote Management
With SSH, administrators can remotely manage IoT devices without the need for physical access. This reduces downtime and simplifies maintenance tasks, leading to increased operational efficiency.
Cost-Effective Solutions
Many SSH tools and services are available for free, making it an affordable option for businesses and individuals looking to implement secure IoT solutions without incurring high costs.
Choosing the Best SSH IoT Remotely Free Options
When selecting SSH solutions for IoT devices, it's important to consider factors such as security, ease of use, and compatibility. Below are some of the best SSH IoT remotely free options available:
OpenSSH
OpenSSH is a widely used open-source SSH client and server software. It offers robust security features and is compatible with a wide range of operating systems, making it an ideal choice for IoT applications.
Bitvise SSH
Bitvise SSH is another popular option that provides both free and paid versions. The free version offers basic functionality, including secure file transfers and remote access, making it suitable for small-scale IoT projects.
WinSCP
WinSCP is a free SFTP and SCP client for Windows that supports SSH connections. It is user-friendly and offers advanced features such as scripting and automation, making it a great choice for managing IoT devices.
Tools for SSH IoT Remotely Free
Several tools are available for implementing SSH in IoT environments. These tools offer a range of features and functionalities to suit different needs and requirements. Below are some of the top tools:
Putty
Putty is a free and lightweight SSH client that is widely used for remote access. It supports multiple protocols, including SSH, Telnet, and Serial, making it versatile for various IoT applications.
Paramiko
Paramiko is a Python library for implementing SSHv2. It allows developers to create custom SSH applications and is particularly useful for automating tasks in IoT environments.
SSH.NET
SSH.NET is a .NET library for implementing SSH functionality. It provides a simple and efficient way to establish SSH connections and execute commands on remote devices.
Setting Up SSH for IoT Devices
Setting up SSH for IoT devices involves several steps, including installing the necessary software, configuring security settings, and testing the connection. Below is a step-by-step guide:
Step 1: Install SSH Client/Server
Install an SSH client or server software on your IoT device. For example, you can use OpenSSH on Linux-based devices or Putty on Windows.
Step 2: Configure Security Settings
Ensure that security settings are properly configured to prevent unauthorized access. This includes setting strong passwords, enabling public key authentication, and disabling root login.
Step 3: Test the Connection
Test the SSH connection by connecting to the IoT device from a remote location. Verify that data transmission is secure and that all functionalities are working as expected.
Securing Your SSH IoT Connections
Securing SSH connections is critical to protecting IoT devices from cyber threats. Below are some best practices for securing SSH IoT connections:
Use Strong Authentication
Implement strong authentication methods, such as public key authentication, to ensure that only authorized users can access your IoT devices.
Enable Encryption
Ensure that all data transmitted over SSH is encrypted using strong encryption algorithms. This prevents attackers from intercepting and reading sensitive information.
Regularly Update Software
Keep your SSH client/server software up to date with the latest security patches and updates to protect against vulnerabilities.
Common Issues and Troubleshooting
While implementing SSH for IoT devices, you may encounter various issues. Below are some common problems and their solutions:
Connection Refused
If you receive a "connection refused" error, ensure that the SSH server is running and that the correct port is being used. Check firewall settings to ensure that the port is not blocked.
Authentication Failed
If authentication fails, verify that the correct username and password are being used. If using public key authentication, ensure that the public key is properly installed on the server.
Slow Connection
Slow SSH connections can be caused by network congestion or server overload. Optimize network settings and ensure that the server has sufficient resources to handle the connection.
SSH IoT Best Practices
To ensure the successful implementation of SSH for IoT devices, follow these best practices:
Regular Audits
Conduct regular audits of your SSH setup to identify and address potential security vulnerabilities.
Limit Access
Restrict access to SSH-enabled IoT devices to only those who need it. Use role-based access control to manage permissions effectively.
Monitor Activity
Monitor SSH activity to detect and respond to suspicious behavior promptly. This can help prevent unauthorized access and data breaches.
Future of SSH in IoT
As the IoT ecosystem continues to grow, the role of SSH in securing remote connections will become increasingly important. Advances in technology and the development of new protocols will enhance the capabilities of SSH, making it even more effective for IoT applications.
Emerging Trends
Some emerging trends in SSH for IoT include the integration of artificial intelligence for threat detection, the use of blockchain for secure authentication, and the development of lightweight SSH protocols for resource-constrained devices.
Conclusion and Next Steps
In conclusion, implementing SSH for IoT devices is essential for ensuring secure and efficient remote access. By choosing the right tools, following best practices, and staying updated with the latest trends, you can harness the full potential of SSH in IoT environments.
We encourage you to take the following steps:
- Explore the tools and resources mentioned in this article to find the best SSH IoT remotely free solutions for your needs.
- Implement security measures to protect your IoT devices from cyber threats.
- Share this article with others who may benefit from the information and leave a comment below with your thoughts and experiences.
Thank you for reading, and we hope this guide has been informative and helpful. For more insights and updates, stay connected with our platform!